2017年3月31日星期五
2017年3月29日星期三
OpenShift_070:为不同的 Project 分配权限
环境:OCP 3.4
假设有两个 Project:project1 和 project 2。要求如下:
普通用户 admin 作为管理员
普通用户 p1admin 作为 project1 管理员
普通用户 p1dev1 作为 project1 的开发人员,有修改权限
普通用户 p1test1 作为 project1 的测试人员,有查看权限
普通用户 p2admin 作为 project2 管理员
普通用户 p2dev1 作为 project2 的开发人员,有修改权限
普通用户 p2test1 作为 project2 的测试人员,有查看权限
1. 以超级管理员身份登录
系统用户 system:admin 是超级管理员
oc login -u system:admin
2. 创建各个账户
htpasswd -b /etc/origin/master/htpasswd admin admin
htpasswd -b /etc/origin/master/htpasswd p1admin p1admin
htpasswd -b /etc/origin/master/htpasswd p2admin p2admin
htpasswd -b /etc/origin/master/htpasswd p1dev1 p1dev1
htpasswd -b /etc/origin/master/htpasswd p1test1 p1test1
htpasswd -b /etc/origin/master/htpasswd p2dev1 p2dev1
htpasswd -b /etc/origin/master/htpasswd p2test1 p2test1
说明:默认情况下,创建账户后,使用 oc login -u <账户> -p <口令> 登录后,该账户就可以创建 Project,创建 Project 后,就成为这个 Project 的管理员,具有 admin 角色。
如果是多 master 结构,需要在每一个 master 节点上创建同样的账户。
下面这个这个命令可以在多个节点生成账户,
ansible -i ansible-hosts masters -m "command" -a " htpasswd -b /etc/origin/master/htpasswd <user> <password>" -b
3. 为 admin 账户授权管理员权限
oadm policy add-cluster-role-to-user admin admin
注意,如果授予 admin cluster-admin 角色,则 admin 为超级管理员。
oadm policy add-cluster-role-to-user cluster-admin admin
cluster-admin 和 admin 角色区别在于 cluster-admin 可以查看和修改 clusterPolicy。
二者都可以管理集群中所有 Project。
常用的授权命令如下:
(1)在当前 Project 下,列出能对指定资源执行指定操作的用户和组
oadm policy who-can verb resource
(2)在当前 Project 下,把指定的角色和用户绑定起来
oadm policy add-role-to-user role username
(3)在当前 Project 下,删除指定用户的指定角色
oadm policy remove-role-from-user role username
(4)在当前 Project 下,在所有的角色中删除指定的用户
oadm policy remove-user username
(5)在当前 Project 下,把指定的角色和组绑定起来
oadm policy add-role-to-group role groupname
(6)在当前 Project 下,删除指定组的指定角色
oadm policy remove-role-from-group role groupname
(7)在当前 Project 下,在所有的角色中删除指定的组
oadm policy remove-group groupname
(8)在集群中所有 Project 下,把指定的角色和用户绑定起来
oadm policy add-cluster-role-to-user role username
(9)在集群中所有 Project 下,删除指定用户的指定角色
oadm policy remove-cluster-role-from-user role username
(10)在集群中所有 Project 下,把指定的角色和组绑定起来
oadm policy add-cluster-role-to-group role groupname
(11)在集群中所有 Project 下,删除指定组的指定角色
oadm policy remove-cluster-role-from-group role groupname
4. 创建各个 Project
oc new-project project1
oc new-project project2
5. 为 project1 分配权限
oc project project1
oc policy add-role-to-user admin p1admin
oc policy add-role-to-user edit p1dev1
oc policy add-role-to-user view p1test1
6. 为 project2 分配权限
oc project project2
oc policy add-role-to-user admin p2admin
oc policy add-role-to-user edit p2dev1
oc policy add-role-to-user view p2test1
7. 一共有多少种 Role ?
oc get clusterroles
输出如下:
NAME
admin
basic-user
cluster-admin
cluster-debugger
cluster-reader
cluster-status
edit
hawkular-metrics-admin
management-infra-admin
registry-admin
registry-editor
registry-viewer
self-access-reviewer
self-provisioner
storage-admin
sudoer
system:build-controller
system:build-strategy-custom
system:build-strategy-docker
system:build-strategy-jenkinspipeline
system:build-strategy-source
system:certificate-signing-controller
system:daemonset-controller
system:deployer
system:deployment-controller
system:deploymentconfig-controller
system:discovery
system:disruption-controller
system:endpoint-controller
system:gc-controller
system:hpa-controller
system:image-auditor
system:image-builder
system:image-pruner
system:image-puller
system:image-pusher
system:image-signer
system:job-controller
system:master
system:namespace-controller
system:node
system:node-admin
system:node-bootstrapper
system:node-proxier
system:node-reader
system:oauth-token-deleter
system:pv-attach-detach-controller
system:pv-binder-controller
system:pv-provisioner-controller
system:pv-recycler-controller
system:registry
system:replicaset-controller
system:replication-controller
system:router
system:sdn-manager
system:sdn-reader
system:service-ingress-ip-controller
system:service-load-balancer-controller
system:service-serving-cert-controller
system:statefulset-controller
system:unidling-controller
system:webhook
view
8. 查看 view 角色具体能操作哪些资源?
oc get clusterpolicy
输出如下:
NAME ROLES LAST MODIFIED
default admin, basic-user, cluster-admin, cluster-debugger, cluster-reader, cluster-status, edit, hawkular-metrics-admin, management-infra-admin, registry-admin, registry-editor, registry-viewer, self-access-reviewer, self-provisioner, storage-admin, sudoer, system:build-controller, system:build-strategy-custom, system:build-strategy-docker, system:build-strategy-jenkinspipeline, system:build-strategy-source, system:certificate-signing-controller, system:daemonset-controller, system:deployer, system:deployment-controller, system:deploymentconfig-controller, system:discovery, system:disruption-controller, system:endpoint-controller, system:gc-controller, system:hpa-controller, system:image-auditor, system:image-builder, system:image-pruner, system:image-puller, system:image-pusher, system:image-signer, system:job-controller, system:master, system:namespace-controller, system:node, system:node-admin, system:node-bootstrapper, system:node-proxier, system:node-reader, system:oauth-token-deleter, system:pv-attach-detach-controller, system:pv-binder-controller, system:pv-provisioner-controller, system:pv-recycler-controller, system:registry, system:replicaset-controller, system:replication-controller, system:router, system:sdn-manager, system:sdn-reader, system:service-ingress-ip-controller, system:service-load-balancer-controller, system:service-serving-cert-controller, system:statefulset-controller, system:unidling-controller, system:webhook, view 2017-05-24 02:57:17 -0400 EDT
8. 查看 clusterPolicy default 具体能操作哪些资源?
oc describe clusterPolicy default
详细定义了每个 Role 可以对哪些 Resources 做哪些操作 Verbs。
9. 查看当前/指定 Project 下的角色和用户、组的绑定关系
oc get rolebinding
输出如下:
NAME ROLE USERS GROUPS SERVICE ACCOUNTS SUBJECTS
admin /admin system:admin
system:deployers /system:deployer deployer
system:image-builders /system:image-builder builder
system:image-pullers /system:image-puller system:serviceaccounts:test
oc describe policyBindings :default
oc describe policyBindings :default -n project1
10. 查看集群角色和用户、组的绑定关系
oc get clusterrolebinding
假设有两个 Project:project1 和 project 2。要求如下:
普通用户 admin 作为管理员
普通用户 p1admin 作为 project1 管理员
普通用户 p1dev1 作为 project1 的开发人员,有修改权限
普通用户 p1test1 作为 project1 的测试人员,有查看权限
普通用户 p2admin 作为 project2 管理员
普通用户 p2dev1 作为 project2 的开发人员,有修改权限
普通用户 p2test1 作为 project2 的测试人员,有查看权限
1. 以超级管理员身份登录
系统用户 system:admin 是超级管理员
oc login -u system:admin
2. 创建各个账户
htpasswd -b /etc/origin/master/htpasswd admin admin
htpasswd -b /etc/origin/master/htpasswd p1admin p1admin
htpasswd -b /etc/origin/master/htpasswd p2admin p2admin
htpasswd -b /etc/origin/master/htpasswd p1dev1 p1dev1
htpasswd -b /etc/origin/master/htpasswd p1test1 p1test1
htpasswd -b /etc/origin/master/htpasswd p2dev1 p2dev1
htpasswd -b /etc/origin/master/htpasswd p2test1 p2test1
说明:默认情况下,创建账户后,使用 oc login -u <账户> -p <口令> 登录后,该账户就可以创建 Project,创建 Project 后,就成为这个 Project 的管理员,具有 admin 角色。
如果是多 master 结构,需要在每一个 master 节点上创建同样的账户。
下面这个这个命令可以在多个节点生成账户,
ansible -i ansible-hosts masters -m "command" -a " htpasswd -b /etc/origin/master/htpasswd
3. 为 admin 账户授权管理员权限
oadm policy add-cluster-role-to-user admin admin
注意,如果授予 admin cluster-admin 角色,则 admin 为超级管理员。
oadm policy add-cluster-role-to-user cluster-admin admin
cluster-admin 和 admin 角色区别在于 cluster-admin 可以查看和修改 clusterPolicy。
二者都可以管理集群中所有 Project。
常用的授权命令如下:
(1)在当前 Project 下,列出能对指定资源执行指定操作的用户和组
oadm policy who-can verb resource
(2)在当前 Project 下,把指定的角色和用户绑定起来
oadm policy add-role-to-user role username
(3)在当前 Project 下,删除指定用户的指定角色
oadm policy remove-role-from-user role username
(4)在当前 Project 下,在所有的角色中删除指定的用户
oadm policy remove-user username
(5)在当前 Project 下,把指定的角色和组绑定起来
oadm policy add-role-to-group role groupname
(6)在当前 Project 下,删除指定组的指定角色
oadm policy remove-role-from-group role groupname
(7)在当前 Project 下,在所有的角色中删除指定的组
oadm policy remove-group groupname
(8)在集群中所有 Project 下,把指定的角色和用户绑定起来
oadm policy add-cluster-role-to-user role username
(9)在集群中所有 Project 下,删除指定用户的指定角色
oadm policy remove-cluster-role-from-user role username
(10)在集群中所有 Project 下,把指定的角色和组绑定起来
oadm policy add-cluster-role-to-group role groupname
(11)在集群中所有 Project 下,删除指定组的指定角色
oadm policy remove-cluster-role-from-group role groupname
4. 创建各个 Project
oc new-project project1
oc new-project project2
5. 为 project1 分配权限
oc project project1
oc policy add-role-to-user admin p1admin
oc policy add-role-to-user edit p1dev1
oc policy add-role-to-user view p1test1
6. 为 project2 分配权限
oc project project2
oc policy add-role-to-user admin p2admin
oc policy add-role-to-user edit p2dev1
oc policy add-role-to-user view p2test1
7. 一共有多少种 Role ?
oc get clusterroles
输出如下:
NAME
admin
basic-user
cluster-admin
cluster-debugger
cluster-reader
cluster-status
edit
hawkular-metrics-admin
management-infra-admin
registry-admin
registry-editor
registry-viewer
self-access-reviewer
self-provisioner
storage-admin
sudoer
system:build-controller
system:build-strategy-custom
system:build-strategy-docker
system:build-strategy-jenkinspipeline
system:build-strategy-source
system:certificate-signing-controller
system:daemonset-controller
system:deployer
system:deployment-controller
system:deploymentconfig-controller
system:discovery
system:disruption-controller
system:endpoint-controller
system:gc-controller
system:hpa-controller
system:image-auditor
system:image-builder
system:image-pruner
system:image-puller
system:image-pusher
system:image-signer
system:job-controller
system:master
system:namespace-controller
system:node
system:node-admin
system:node-bootstrapper
system:node-proxier
system:node-reader
system:oauth-token-deleter
system:pv-attach-detach-controller
system:pv-binder-controller
system:pv-provisioner-controller
system:pv-recycler-controller
system:registry
system:replicaset-controller
system:replication-controller
system:router
system:sdn-manager
system:sdn-reader
system:service-ingress-ip-controller
system:service-load-balancer-controller
system:service-serving-cert-controller
system:statefulset-controller
system:unidling-controller
system:webhook
view
8. 查看 view 角色具体能操作哪些资源?
oc describe clusterrole view
输出如下:
Name: view
Namespace:
Created: 7 weeks ago
Labels:
Annotations: openshift.io/description=A user who can view but not edit any resources within the project. They can not view secrets or membership.
Verbs Non-Resource URLs Extension Resource Names API Groups Resources
[get list watch] [] [] [] [configmaps endpoints persistentvolumeclaims pods replicationcontrollers serviceaccounts services]
[get list watch] [] [] [] [bindings events limitranges namespaces namespaces/status pods/log pods/status replicationcontrollers/status resourcequotas resourcequotas/status]
[get list watch] [] [] [autoscaling] [horizontalpodautoscalers]
[get list watch] [] [] [batch] [cronjobs jobs scheduledjobs]
[get list watch] [] [] [extensions] [deployments deployments/scale horizontalpodautoscalers jobs replicasets replicasets/scale]
[get list watch] [] [] [extensions] [daemonsets]
[get list watch] [] [] [apps] [statefulsets]
[get list watch] [] [] [] [buildconfigs buildconfigs/webhooks builds]
[get list watch] [] [] [] [builds/log]
[view] [] [] [build.openshift.io] [jenkins]
[get list watch] [] [] [] [deploymentconfigs deploymentconfigs/scale]
[get list watch] [] [] [] [deploymentconfigs/log deploymentconfigs/status]
[get list watch] [] [] [] [imagestreamimages imagestreammappings imagestreams imagestreamtags]
[get list watch] [] [] [] [imagestreams/status]
[get] [] [] [] [projects]
[get list watch] [] [] [] [appliedclusterresourcequotas]
[get list watch] [] [] [] [routes]
[get list watch] [] [] [] [routes/status]
[get list watch] [] [] [] [processedtemplates templateconfigs templates]
[get list watch] [] [] [] [buildlogs]
[get list watch] [] [] [] [resourcequotausages]
8. 查看 clusterPolicy 拥有的角色输出如下:
Name: view
Namespace:
Created: 7 weeks ago
Labels:
Annotations: openshift.io/description=A user who can view but not edit any resources within the project. They can not view secrets or membership.
Verbs Non-Resource URLs Extension Resource Names API Groups Resources
[get list watch] [] [] [] [configmaps endpoints persistentvolumeclaims pods replicationcontrollers serviceaccounts services]
[get list watch] [] [] [] [bindings events limitranges namespaces namespaces/status pods/log pods/status replicationcontrollers/status resourcequotas resourcequotas/status]
[get list watch] [] [] [autoscaling] [horizontalpodautoscalers]
[get list watch] [] [] [batch] [cronjobs jobs scheduledjobs]
[get list watch] [] [] [extensions] [deployments deployments/scale horizontalpodautoscalers jobs replicasets replicasets/scale]
[get list watch] [] [] [extensions] [daemonsets]
[get list watch] [] [] [apps] [statefulsets]
[get list watch] [] [] [] [buildconfigs buildconfigs/webhooks builds]
[get list watch] [] [] [] [builds/log]
[view] [] [] [build.openshift.io] [jenkins]
[get list watch] [] [] [] [deploymentconfigs deploymentconfigs/scale]
[get list watch] [] [] [] [deploymentconfigs/log deploymentconfigs/status]
[get list watch] [] [] [] [imagestreamimages imagestreammappings imagestreams imagestreamtags]
[get list watch] [] [] [] [imagestreams/status]
[get] [] [] [] [projects]
[get list watch] [] [] [] [appliedclusterresourcequotas]
[get list watch] [] [] [] [routes]
[get list watch] [] [] [] [routes/status]
[get list watch] [] [] [] [processedtemplates templateconfigs templates]
[get list watch] [] [] [] [buildlogs]
[get list watch] [] [] [] [resourcequotausages]
oc get clusterpolicy
输出如下:
NAME ROLES LAST MODIFIED
default admin, basic-user, cluster-admin, cluster-debugger, cluster-reader, cluster-status, edit, hawkular-metrics-admin, management-infra-admin, registry-admin, registry-editor, registry-viewer, self-access-reviewer, self-provisioner, storage-admin, sudoer, system:build-controller, system:build-strategy-custom, system:build-strategy-docker, system:build-strategy-jenkinspipeline, system:build-strategy-source, system:certificate-signing-controller, system:daemonset-controller, system:deployer, system:deployment-controller, system:deploymentconfig-controller, system:discovery, system:disruption-controller, system:endpoint-controller, system:gc-controller, system:hpa-controller, system:image-auditor, system:image-builder, system:image-pruner, system:image-puller, system:image-pusher, system:image-signer, system:job-controller, system:master, system:namespace-controller, system:node, system:node-admin, system:node-bootstrapper, system:node-proxier, system:node-reader, system:oauth-token-deleter, system:pv-attach-detach-controller, system:pv-binder-controller, system:pv-provisioner-controller, system:pv-recycler-controller, system:registry, system:replicaset-controller, system:replication-controller, system:router, system:sdn-manager, system:sdn-reader, system:service-ingress-ip-controller, system:service-load-balancer-controller, system:service-serving-cert-controller, system:statefulset-controller, system:unidling-controller, system:webhook, view 2017-05-24 02:57:17 -0400 EDT
8. 查看 clusterPolicy default 具体能操作哪些资源?
oc describe clusterPolicy default
详细定义了每个 Role 可以对哪些 Resources 做哪些操作 Verbs。
9. 查看当前/指定 Project 下的角色和用户、组的绑定关系
oc get rolebinding
输出如下:
NAME ROLE USERS GROUPS SERVICE ACCOUNTS SUBJECTS
admin /admin system:admin
system:deployers /system:deployer deployer
system:image-builders /system:image-builder builder
system:image-pullers /system:image-puller system:serviceaccounts:test
oc describe policyBindings :default
oc describe policyBindings :default -n project1
10. 查看集群角色和用户、组的绑定关系
oc get clusterrolebinding
OpenShift_069:构建 Spring Boot Builder Image(基于 centos7)
环境:MAC OS X 10.12.3 + Docker 1.13.1 + S2I 1.1.5
本文构建一个 spring boot builder image。
以下操作均在 MAC 机器上执行。
1. 创建 S2I 目录结构
s2i create spring-boot-centos7 s2i-spring-boot
说明:这里 spring-boot-centos7 是 builder image 名称,s2i-spring-boot 是目录名称。
2. 下载并解压 jdk 1.8 和 maven 3
tar zxvf jdk-8u121-linux-x64.tar.gz
mv jdk1.8.0_121 jdk
tar zxvf apache-maven-3.3.9-bin.tar.gz
mv apache-maven-3.3.9 maven
3. 为了能够安装软件,下载 CentOS7 repo
wget http://mirrors.163.com/.help/CentOS7-Base-163.repo
4. 定义 Docker file
内容如下:
FROM openshift/base-centos7
EXPOSE 8080
LABEL io.k8s.description="Platform for building and running Spring Boot applications" \
io.k8s.display-name="Spring Boot Maven 3" \
io.openshift.expose-services="8080:http" \
io.openshift.tags="builder,java,java8,maven,maven3,springboot"
COPY CentOS7-Base-163.repo /etc/yum.repos.d/CentOS7-Base-163.repo
RUN yum update -y && \
yum install -y curl wget git iproute iputils net-tools bash-completion && \
yum clean all
# 切换镜像的目录,进入 /usr 目录
WORKDIR /usr
# 在 /usr 下创建 java 目录,用来存放 jdk
RUN mkdir java
# 切换镜像的目录至 /usr/java
WORKDIR /usr/java
# 在 /usr/java 下创建 jdk 目录,用来存放 jdk 文件
RUN mkdir jdk
# 切换镜像的目录至 /usr/java/jdk
WORKDIR /usr/java/jdk
# 将宿主机的 jdk 目录下的全部文件考入至镜像的 /usr/java/jdk 目录下
ADD jdk /usr/java/jdk
# 切换镜像的目录至 /usr/share
WORKDIR /usr/share
# 在 /usr/share 下创建 maven 目录,用来存放 maven 文件
RUN mkdir maven
# 将宿主机的 maven 目录下的全部文件考入至镜像的 /opt/face 目录下
ADD maven /usr/share/maven
RUN ln -s /usr/share/maven/bin/mvn /usr/bin/mvn
# 设置时区,容器时间和宿主机时间同步
RUN rm -f /etc/localtime && ln -s /usr/share/zoneinfo/Asia/Shanghai /etc/localtime
# 切换镜像的目录至 /opt/app-root/src
WORKDIR /opt/app-root/src
# 设置环境变量
ENV JAVA_VERSON=1.8.0_121
ENV MAVEN_VERSION=3.3.9
ENV JAVA_HOME=/usr/java/jdk
ENV JAVA_BIN=/usr/java/jdk/bin
ENV PATH=$PATH:$JAVA_HOME/bin
ENV CLASSPATH=.:$JAVA_HOME/lib/dt.jar:$JAVA_HOME/lib/tools.jar
ENV MAVEN_HOME=/usr/share/maven
# Add configuration files, bashrc and other tweaks
COPY ./s2i/bin/ $STI_SCRIPTS_PATH
RUN chown -R 1001:1001 /opt/app-root
USER 1001
# Set the default CMD to print the usage of the language image
CMD $STI_SCRIPTS_PATH/usage
5. 定义 s2i/bin/assemble
#!/bin/bash
set -e
echo "---> Installing application source"
cp -Rf /tmp/src/. ./
echo "---> Building Spring Boot application from source"
echo "--> # MVN_ARGS = $MVN_ARGS"
if [ -f "mvnw" ]; then
./mvnw clean install $MVN_ARGS
else
mvn clean install $MVN_ARGS
fi
# Fix source directory permissions
fix-permissions ./
6. 定义 s2i/bin/run
#!/bin/bash
set -e
APP_TARGET=${APP_TARGET:-target}
echo "---> Starting Spring Boot application"
echo "--> # APP_TARGET = $APP_TARGET"
echo "--> # JAVA_OPTS = $JAVA_OPTS"
echo "---> Running application from jar ($(find $APP_TARGET -name *.jar)) ..."
java $JAVA_OPTS -jar `find $APP_TARGET -name *.jar`
7. 定义 s2i/bin/usage
#!/bin/sh -e
cat <This is a STI springboot maven3 centos base image:
To use it, install STI: https://github.com/openshift/source-to-image
Sample invocation:
sti build git://github.com/codecentric/springboot-sample-app spring-boot-centos7 springboot-sample-app
You can then run the resulting image via:
docker run -p 8080:8080 springboot-sample-app
EOF
8. 构建 spring boot builder image
make build
或者
docker build -t spring-boot-centos7 .
构建后,启动镜像,检查软件是否都安装了
docker run -it spring-boot-centos7 bash
9. 使用 spring boot builder image 构建应用镜像
s2i build git://github.com/codecentric/springboot-sample-app spring-boot-centos7 springboot-sample-app
这里有一个小问题,就是每次构建应用镜像,都会从网上下载 maven 构件,非常耽误时间。
能不能指向自己私有的 maven 仓库呢?
想一想 maven 的知识,嗯,修改 /usr/share/maven/conf/setting.xml 文件内容。
把本机的 ~/.m2/setting.xml 内容复制过去,
修改这一行,指向镜像中自己的 repository
<localRepository>/opt/app-root/src/.m2/repository</localRepository>
还有别忘了把 localhost 改成 IP 地址,如果有的话。
10. 启动应用镜像
docker run -p 8080:8080 springboot-sample-app
访问 http://localhost:8080
至此,说明 spring boot builder image 构建成功!
参考文献:
1. https://blog.codecentric.de/en/2016/03/deploy-spring-boot-applications-openshift/
2. https://hub.docker.com/r/codecentric/springboot-maven3-centos/
3. https://github.com/codecentric/springboot-maven3-centos
4. https://blog.openshift.com/using-spring-boot-on-openshift/
5. https://blog.openshift.com/using-openshift-enterprise-grade-spring-boot-deployments/
本文构建一个 spring boot builder image。
以下操作均在 MAC 机器上执行。
1. 创建 S2I 目录结构
s2i create spring-boot-centos7 s2i-spring-boot
说明:这里 spring-boot-centos7 是 builder image 名称,s2i-spring-boot 是目录名称。
2. 下载并解压 jdk 1.8 和 maven 3
tar zxvf jdk-8u121-linux-x64.tar.gz
mv jdk1.8.0_121 jdk
tar zxvf apache-maven-3.3.9-bin.tar.gz
mv apache-maven-3.3.9 maven
3. 为了能够安装软件,下载 CentOS7 repo
wget http://mirrors.163.com/.help/CentOS7-Base-163.repo
4. 定义 Docker file
内容如下:
FROM openshift/base-centos7
EXPOSE 8080
LABEL io.k8s.description="Platform for building and running Spring Boot applications" \
io.k8s.display-name="Spring Boot Maven 3" \
io.openshift.expose-services="8080:http" \
io.openshift.tags="builder,java,java8,maven,maven3,springboot"
COPY CentOS7-Base-163.repo /etc/yum.repos.d/CentOS7-Base-163.repo
RUN yum update -y && \
yum install -y curl wget git iproute iputils net-tools bash-completion && \
yum clean all
# 切换镜像的目录,进入 /usr 目录
WORKDIR /usr
# 在 /usr 下创建 java 目录,用来存放 jdk
RUN mkdir java
# 切换镜像的目录至 /usr/java
WORKDIR /usr/java
# 在 /usr/java 下创建 jdk 目录,用来存放 jdk 文件
RUN mkdir jdk
# 切换镜像的目录至 /usr/java/jdk
WORKDIR /usr/java/jdk
# 将宿主机的 jdk 目录下的全部文件考入至镜像的 /usr/java/jdk 目录下
ADD jdk /usr/java/jdk
# 切换镜像的目录至 /usr/share
WORKDIR /usr/share
# 在 /usr/share 下创建 maven 目录,用来存放 maven 文件
RUN mkdir maven
# 将宿主机的 maven 目录下的全部文件考入至镜像的 /opt/face 目录下
ADD maven /usr/share/maven
RUN ln -s /usr/share/maven/bin/mvn /usr/bin/mvn
# 设置时区,容器时间和宿主机时间同步
RUN rm -f /etc/localtime && ln -s /usr/share/zoneinfo/Asia/Shanghai /etc/localtime
# 切换镜像的目录至 /opt/app-root/src
WORKDIR /opt/app-root/src
# 设置环境变量
ENV JAVA_VERSON=1.8.0_121
ENV MAVEN_VERSION=3.3.9
ENV JAVA_HOME=/usr/java/jdk
ENV JAVA_BIN=/usr/java/jdk/bin
ENV PATH=$PATH:$JAVA_HOME/bin
ENV CLASSPATH=.:$JAVA_HOME/lib/dt.jar:$JAVA_HOME/lib/tools.jar
ENV MAVEN_HOME=/usr/share/maven
# Add configuration files, bashrc and other tweaks
COPY ./s2i/bin/ $STI_SCRIPTS_PATH
RUN chown -R 1001:1001 /opt/app-root
USER 1001
# Set the default CMD to print the usage of the language image
CMD $STI_SCRIPTS_PATH/usage
5. 定义 s2i/bin/assemble
#!/bin/bash
set -e
echo "---> Installing application source"
cp -Rf /tmp/src/. ./
echo "---> Building Spring Boot application from source"
echo "--> # MVN_ARGS = $MVN_ARGS"
if [ -f "mvnw" ]; then
./mvnw clean install $MVN_ARGS
else
mvn clean install $MVN_ARGS
fi
# Fix source directory permissions
fix-permissions ./
6. 定义 s2i/bin/run
#!/bin/bash
set -e
APP_TARGET=${APP_TARGET:-target}
echo "---> Starting Spring Boot application"
echo "--> # APP_TARGET = $APP_TARGET"
echo "--> # JAVA_OPTS = $JAVA_OPTS"
echo "---> Running application from jar ($(find $APP_TARGET -name *.jar)) ..."
java $JAVA_OPTS -jar `find $APP_TARGET -name *.jar`
7. 定义 s2i/bin/usage
#!/bin/sh -e
cat <
To use it, install STI: https://github.com/openshift/source-to-image
Sample invocation:
sti build git://github.com/codecentric/springboot-sample-app spring-boot-centos7 springboot-sample-app
You can then run the resulting image via:
docker run -p 8080:8080 springboot-sample-app
EOF
8. 构建 spring boot builder image
make build
或者
docker build -t spring-boot-centos7 .
构建后,启动镜像,检查软件是否都安装了
docker run -it spring-boot-centos7 bash
9. 使用 spring boot builder image 构建应用镜像
s2i build git://github.com/codecentric/springboot-sample-app spring-boot-centos7 springboot-sample-app
修改这一行,指向镜像中自己的 repository
<localRepository>/opt/app-root/src/.m2/repository</localRepository>
还有别忘了把 localhost 改成 IP 地址,如果有的话。
重新构建 builder image,重新构建应用镜像,这次将会下载到自己私有的 maven 仓库,下次构建应用镜像不用重新下载 maven 构件,速度快了很多!
10. 启动应用镜像
docker run -p 8080:8080 springboot-sample-app
访问 http://localhost:8080
至此,说明 spring boot builder image 构建成功!
参考文献:
1. https://blog.codecentric.de/en/2016/03/deploy-spring-boot-applications-openshift/
2. https://hub.docker.com/r/codecentric/springboot-maven3-centos/
3. https://github.com/codecentric/springboot-maven3-centos
4. https://blog.openshift.com/using-spring-boot-on-openshift/
5. https://blog.openshift.com/using-openshift-enterprise-grade-spring-boot-deployments/
2017年3月28日星期二
SpringBoot_001:运行官网的 Helloword 例子
环境:MAC OS X 10.12.3 + JDK 1.8 + Spring Boot
本文旨在快速运行一个 Spring Boot 例子。
1. 克隆代码
cd ~/mygit
git clone https://github.com/spring-guides/gs-spring-boot.git
2. 构建并运行
. ~/setJdk8Env.sh
cd gs-spring-boot/initial
mvn package && java -jar target/gs-spring-boot-0.1.0.jar
3. 访问 localhost:8080
curl localhost:8080
输出如下:
Greetings from Spring Boot!
参考文献:
1. http://spring.io/guides/gs/spring-boot/
本文旨在快速运行一个 Spring Boot 例子。
1. 克隆代码
cd ~/mygit
git clone https://github.com/spring-guides/gs-spring-boot.git
2. 构建并运行
. ~/setJdk8Env.sh
cd gs-spring-boot/initial
mvn package && java -jar target/gs-spring-boot-0.1.0.jar
3. 访问 localhost:8080
curl localhost:8080
输出如下:
Greetings from Spring Boot!
参考文献:
1. http://spring.io/guides/gs/spring-boot/
OpenShift_068:构建一个简单的 S2I Builder Image(基于 centos7)
环境:MAC OS X 10.12.3 + Docker 1.13.1 + S2I 1.1.5
本文构建一个 lighttpd builder image,比较简单,旨在了解构建 S2I Builder Image 的主要步骤和原理。
以下操作均在 MAC 机器上执行。
1. 下载并安装 S2I 工具
下载地址:https://github.com/openshift/source-to-image/releases
下载介质:source-to-image-v1.1.5-4dd7721-darwin-amd64.tar.gz
安装
tar zxvf source-to-image-v1.1.5-4dd7721-darwin-amd64.tar.gz
mv s2i sti /usr/local/bin/
2. 创建 S2I 目录结构
s2i create lighttpd-centos7 s2i-lighttpd
说明:这里 lighttpd-centos7 是 builder image 名称,s2i-lighttpd 是目录名称。
在 s2i-lighttpd 目录下有:
(1)Dockerfile – 定义 builder image
(2)Makefile – 包含构建 builder image 和测试 builder image 的脚本
(3)test/
(3.1)run – 测试脚本
(3.2)test-app/ – 要测试应用
(4).s2i/bin/
(4.1)assemble – 构建应用的脚本
(4.2)run – 运行应用的脚本
(4.3)save-artifacts – 增量构建的脚本
(4.4)usage – 如何使用 builder image 的帮助脚本
3. 定义 Docker file
内容如下:
# We are basing our builder image on openshift base-centos7 image
FROM openshift/base-centos7
# Inform users who's the maintainer of this builder image
MAINTAINER Ma Ping <pma@redhat.com>
# Inform about software versions being used inside the builder
ENV LIGHTTPD_VERSION=1.4.45
# Set labels used in OpenShift to describe the builder images
LABEL io.k8s.description="Platform for serving static HTML files" \
io.k8s.display-name="Lighttpd 1.4.45" \
io.openshift.expose-services="8080:http" \
io.openshift.tags="builder,html,lighttpd"
# Install the required software, namely Lighttpd and
COPY CentOS7-Base-163.repo /etc/yum.repos.d/CentOS7-Base-163.repo
RUN yum install -y epel-release && \
yum install -y lighttpd && \
# clean yum cache files, as they are not needed and will only make the image bigger in the end
yum clean all -y
# Defines the location of the S2I
# Although this is defined in openshift/base-centos7 image it's repeated here
# to make it clear why the following COPY operation is happening
LABEL io.openshift.s2i.scripts-url=image:///usr/local/s2i
# Copy the S2I scripts from ./.s2i/bin/ to /usr/local/s2i when making the builder image
COPY ./.s2i/bin/ /usr/local/s2i
# Copy the lighttpd configuration file
COPY ./etc/ /opt/app-root/etc
# Drop the root user and make the content of /opt/app-root owned by user 1001
RUN chown -R 1001:1001 /opt/app-root
# Set the default user for the image, the user itself was created in the base image
USER 1001
# Specify the ports the final image will expose
EXPOSE 8080
# Set the default CMD to print the usage of the image, if somebody does docker run
CMD ["usage"]
4. 定义 s2i/bin/assemble
内容如下:
#!/bin/bash -e
#
# S2I assemble script for the 'lighttpd-centos7' image.
# The 'assemble' script builds your application source ready to run.
#
# For more information refer to the documentation:
# https://github.com/openshift/source-to-image/blob/master/docs/builder_image.md
#
echo "---> Installing application source"
cp -Rf /tmp/src/. ./
说明:默认情况下,s2i 构建过程会把应用源代码放在 /tmp/src 目录下。
如果要修改源代码放置目录,可以指定 io.openshift.s2i.destination label 或者在命令行增加 --destination 参数。
这里的当前目录 ./ 表示的是 openshift/base-centos7 的工作目录,即 /opt/app-root/src。
5. 定义 s2i/bin/run
内容如下:
#!/bin/bash -e
#
# S2I run script for the 'lighttpd-centos7' image.
# The run script executes the server that runs your application.
#
# For more information see the documentation:
# https://github.com/openshift/source-to-image/blob/master/docs/builder_image.md
#
exec lighttpd -D -f /opt/app-root/etc/lighttpd.conf
6. 定义 s2i/bin/usage
内容如下:
#!/bin/bash -e
cat <<EOF
This is the lighttpd-centos7 S2I image:
To use it, install S2I: https://github.com/openshift/source-to-image
Sample invocation:
s2i build https://github.com/soltysh/sti-lighttpd.git --context-dir=test/test-app/ lighttpd-centos7 sample-app
You can then run the resulting image via:
docker run -p 8080:8080 sample-app
EOF
7. 创建 etc/lighttpd.conf,Dockerfile 中要复制此文件
内容如下:
# directory where the documents will be served from
server.document-root = "/opt/app-root/src"
# port the server listens on
server.port = 8080
# default file if none is provided in the URL
index-file.names = ( "index.html" )
# configure specific mimetypes, otherwise application/octet-stream will be used for every file
mimetype.assign = (
".html" => "text/html",
".txt" => "text/plain",
".jpg" => "image/jpeg",
".png" => "image/png"
)
说明:这是一个很简单的 lighttpd 配置文件,配置了如下信息:
(1)服务内容路径:/opt/app-root/src
(2)监听端口:8080
(3)默认欢迎文件:index.html
(4)支持的 mimetype 映射类型
8. 定义 test/test-app/index.html
内容如下:
<!doctype html>
<html>
<head>
<title>test-app</title>
</head>
<body>
<h1>Hello from lighttpd served index.html!</h1>
</body>
</html>
9. 为了能够安装 lighttpd,下载 CentOS7 repo
wget http://mirrors.163.com/.help/CentOS7-Base-163.repo
10. 构建 lighttpd builder image
make build
或者
docker build -t lighttpd-centos7 .
11. 使用 lighttpd builder image 构建应用镜像
s2i build test/test-app/ lighttpd-centos7 sample-app
12. 启动应用镜像
docker run -p 8080:8080 sample-app
访问 http://localhost:8080,显示 Hello from lighttpd served index.html!
至此,说明 lighttpd builder image 构建成功!
参考文献:
1. https://blog.openshift.com/create-s2i-builder-image/
本文构建一个 lighttpd builder image,比较简单,旨在了解构建 S2I Builder Image 的主要步骤和原理。
以下操作均在 MAC 机器上执行。
1. 下载并安装 S2I 工具
下载地址:https://github.com/openshift/source-to-image/releases
下载介质:source-to-image-v1.1.5-4dd7721-darwin-amd64.tar.gz
安装
tar zxvf source-to-image-v1.1.5-4dd7721-darwin-amd64.tar.gz
mv s2i sti /usr/local/bin/
2. 创建 S2I 目录结构
s2i create lighttpd-centos7 s2i-lighttpd
说明:这里 lighttpd-centos7 是 builder image 名称,s2i-lighttpd 是目录名称。
在 s2i-lighttpd 目录下有:
(1)Dockerfile – 定义 builder image
(2)Makefile – 包含构建 builder image 和测试 builder image 的脚本
(3)test/
(3.1)run – 测试脚本
(3.2)test-app/ – 要测试应用
(4).s2i/bin/
(4.1)assemble – 构建应用的脚本
(4.2)run – 运行应用的脚本
(4.3)save-artifacts – 增量构建的脚本
(4.4)usage – 如何使用 builder image 的帮助脚本
3. 定义 Docker file
内容如下:
# We are basing our builder image on openshift base-centos7 image
FROM openshift/base-centos7
# Inform users who's the maintainer of this builder image
MAINTAINER Ma Ping <pma@redhat.com>
# Inform about software versions being used inside the builder
ENV LIGHTTPD_VERSION=1.4.45
# Set labels used in OpenShift to describe the builder images
LABEL io.k8s.description="Platform for serving static HTML files" \
io.k8s.display-name="Lighttpd 1.4.45" \
io.openshift.expose-services="8080:http" \
io.openshift.tags="builder,html,lighttpd"
# Install the required software, namely Lighttpd and
COPY CentOS7-Base-163.repo /etc/yum.repos.d/CentOS7-Base-163.repo
RUN yum install -y epel-release && \
yum install -y lighttpd && \
# clean yum cache files, as they are not needed and will only make the image bigger in the end
yum clean all -y
# Defines the location of the S2I
# Although this is defined in openshift/base-centos7 image it's repeated here
# to make it clear why the following COPY operation is happening
LABEL io.openshift.s2i.scripts-url=image:///usr/local/s2i
# Copy the S2I scripts from ./.s2i/bin/ to /usr/local/s2i when making the builder image
COPY ./.s2i/bin/ /usr/local/s2i
# Copy the lighttpd configuration file
COPY ./etc/ /opt/app-root/etc
# Drop the root user and make the content of /opt/app-root owned by user 1001
RUN chown -R 1001:1001 /opt/app-root
# Set the default user for the image, the user itself was created in the base image
USER 1001
# Specify the ports the final image will expose
EXPOSE 8080
# Set the default CMD to print the usage of the image, if somebody does docker run
CMD ["usage"]
4. 定义 s2i/bin/assemble
内容如下:
#!/bin/bash -e
#
# S2I assemble script for the 'lighttpd-centos7' image.
# The 'assemble' script builds your application source ready to run.
#
# For more information refer to the documentation:
# https://github.com/openshift/source-to-image/blob/master/docs/builder_image.md
#
echo "---> Installing application source"
cp -Rf /tmp/src/. ./
说明:默认情况下,s2i 构建过程会把应用源代码放在 /tmp/src 目录下。
如果要修改源代码放置目录,可以指定 io.openshift.s2i.destination label 或者在命令行增加 --destination 参数。
这里的当前目录 ./ 表示的是 openshift/base-centos7 的工作目录,即 /opt/app-root/src。
5. 定义 s2i/bin/run
内容如下:
#!/bin/bash -e
#
# S2I run script for the 'lighttpd-centos7' image.
# The run script executes the server that runs your application.
#
# For more information see the documentation:
# https://github.com/openshift/source-to-image/blob/master/docs/builder_image.md
#
exec lighttpd -D -f /opt/app-root/etc/lighttpd.conf
6. 定义 s2i/bin/usage
内容如下:
#!/bin/bash -e
cat <<EOF
This is the lighttpd-centos7 S2I image:
To use it, install S2I: https://github.com/openshift/source-to-image
Sample invocation:
s2i build https://github.com/soltysh/sti-lighttpd.git --context-dir=test/test-app/ lighttpd-centos7 sample-app
You can then run the resulting image via:
docker run -p 8080:8080 sample-app
EOF
7. 创建 etc/lighttpd.conf,Dockerfile 中要复制此文件
内容如下:
# directory where the documents will be served from
server.document-root = "/opt/app-root/src"
# port the server listens on
server.port = 8080
# default file if none is provided in the URL
index-file.names = ( "index.html" )
# configure specific mimetypes, otherwise application/octet-stream will be used for every file
mimetype.assign = (
".html" => "text/html",
".txt" => "text/plain",
".jpg" => "image/jpeg",
".png" => "image/png"
)
说明:这是一个很简单的 lighttpd 配置文件,配置了如下信息:
(1)服务内容路径:/opt/app-root/src
(2)监听端口:8080
(3)默认欢迎文件:index.html
(4)支持的 mimetype 映射类型
8. 定义 test/test-app/index.html
内容如下:
<!doctype html>
<html>
<head>
<title>test-app</title>
</head>
<body>
<h1>Hello from lighttpd served index.html!</h1>
</body>
</html>
9. 为了能够安装 lighttpd,下载 CentOS7 repo
wget http://mirrors.163.com/.help/CentOS7-Base-163.repo
10. 构建 lighttpd builder image
make build
或者
docker build -t lighttpd-centos7 .
11. 使用 lighttpd builder image 构建应用镜像
s2i build test/test-app/ lighttpd-centos7 sample-app
12. 启动应用镜像
docker run -p 8080:8080 sample-app
访问 http://localhost:8080,显示 Hello from lighttpd served index.html!
至此,说明 lighttpd builder image 构建成功!
参考文献:
1. https://blog.openshift.com/create-s2i-builder-image/
2017年3月27日星期一
OpenShift_067:使用 Hawkular APM 监控容器中的 Java Web 应用(Template 方式)
环境:OCP 3.4
使用 Dockerfile 方式部署 Java Web 应用太麻烦,而且不通用。
本文使用 Template 方式部署。
1. 创建 Builder Image
mkdir tomcat8-hawkular-apm
cd tomcat8-hawkular-apm
vim Dockerfile
内容如下:
FROM registry.example.com:5000/jboss-webserver-3/webserver30-tomcat8-openshift:latest
COPY hawkular-apm-agent-opentracing.jar $HOME
USER root
RUN chmod 777 $HOME/hawkular-apm-agent-opentracing.jar
RUN chmod -R 777 $HOME
USER 1001
说明:这里以 jboss-webserver-3/webserver30-tomcat8-openshift:latest 作为 Base Image。
docker build -t="maping930883/tomcat8-hawkular-apm" .
2. 修改 Tag,并 Push 到本地镜像仓库
docker tag maping930883/tomcat8-hawkular-apm:latest registry.example.com:5000/maping930883/tomcat8-hawkular-apm:latest
docker push registry.example.com:5000/maping930883/tomcat8-hawkular-apm:latest
3. 创建 Image Stream
参考 jboss-webserver30-tomcat8-openshift Image Stream
oc export is jboss-webserver30-tomcat8-openshift -n openshift -o json
修改完后,创建自己的 Image Stream
oc create -f tomcat8-hawkular-apm-is.json -n openshift
其中 tomcat8-hawkular-apm-is.json 内容如下:
{
"kind": "ImageStream",
"apiVersion": "v1",
"metadata": {
"name": "tomcat8-hawkular-apm",
"creationTimestamp": null
},
"spec": {
"dockerImageRepository": "registry.example.com:5000/maping930883/tomcat8-hawkular-apm",
"tags": [
{
"name": "latest",
"annotations": null,
"from": {
"kind": "DockerImage",
"name": "registry.example.com:5000/maping930883/tomcat8-hawkular-apm"
},
"generation": 1,
"importPolicy": {
"insecure": true
}
}
]
}
}
确认 TAGS 已经打上,执行 oc get is tomcat8-hawkular-apm -n openshift
输出如下:
NAME DOCKER REPO TAGS UPDATED
tomcat8-hawkular-apm registry.example.com:5000/maping930883/tomcat8-hawkular-apm latest 3 hours ago
如果 TAGS 没打上,执行 oc import-image tomcat8-hawkular-apm --insecure -n openshift
4. 创建 Template
参考 jws30-tomcat8-basic-s2i 模板
oc export template jws30-tomcat8-basic-s2i -n openshift -o json
修改 jws30-tomcat8-basic-s2i 模板
oc edit template jws30-tomcat8-basic-s2i -n openshift
把 name: jboss-webserver30-tomcat8-openshift:1.2
改为 name: jboss-webserver30-tomcat8-openshift:latest
修改完后,创建自己的模板
oc create -f tomcat8-hawkular-apm-s2i-template.json -n openshift
其中 tomcat8-hawkular-apm-s2i-template.json 内容如下:
{
"kind": "Template",
"apiVersion": "v1",
"metadata": {
"name": "tomcat8-hawkluar-apm-s2i",
"creationTimestamp": null,
"annotations": {
"iconClass": "icon-java",
"description": "Application template for Java Web applications built using S2I and supporting Hawkular APM.",
"tags": "java,tomcat8,hawkular,apm",
"version": "1.0"
}
},
"objects": [
{
"apiVersion": "v1",
"kind": "Service",
"metadata": {
"annotations": {
"description": "The web server's http port."
},
"labels": {
"application": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
},
"spec": {
"ports": [
{
"port": 8080,
"targetPort": 8080
}
],
"selector": {
"deploymentConfig": "${APPLICATION_NAME}"
}
}
},
{
"apiVersion": "v1",
"id": "${APPLICATION_NAME}-http",
"kind": "Route",
"metadata": {
"annotations": {
"description": "Route for application's http service."
},
"labels": {
"application": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
},
"spec": {
"host": "${HOSTNAME_HTTP}",
"to": {
"name": "${APPLICATION_NAME}"
}
}
},
{
"apiVersion": "v1",
"kind": "ImageStream",
"metadata": {
"labels": {
"application": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
}
},
{
"apiVersion": "v1",
"kind": "BuildConfig",
"metadata": {
"labels": {
"application": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
},
"spec": {
"output": {
"to": {
"kind": "ImageStreamTag",
"name": "${APPLICATION_NAME}:latest"
}
},
"source": {
"contextDir": "${CONTEXT_DIR}",
"git": {
"ref": "${SOURCE_REPOSITORY_REF}",
"uri": "${SOURCE_REPOSITORY_URL}"
},
"type": "Git"
},
"strategy": {
"sourceStrategy": {
"forcePull": true,
"from": {
"kind": "ImageStreamTag",
"name": "tomcat8-hawkular-apm:latest",
"namespace": "${IMAGE_STREAM_NAMESPACE}"
},
"env": [
{
"name": "MAVEN_MIRROR_URL",
"value": "${MAVEN_MIRROR_URL}"
}
]
},
"type": "Source"
},
"triggers": [
{
"github": {
"secret": "${GITHUB_WEBHOOK_SECRET}"
},
"type": "GitHub"
},
{
"generic": {
"secret": "${GENERIC_WEBHOOK_SECRET}"
},
"type": "Generic"
},
{
"imageChange": {},
"type": "ImageChange"
},
{
"type": "ConfigChange"
}
]
}
},
{
"apiVersion": "v1",
"kind": "DeploymentConfig",
"metadata": {
"labels": {
"application": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
},
"spec": {
"replicas": 1,
"selector": {
"deploymentConfig": "${APPLICATION_NAME}"
},
"strategy": {
"type": "Recreate"
},
"template": {
"metadata": {
"labels": {
"application": "${APPLICATION_NAME}",
"deploymentConfig": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
},
"spec": {
"containers": [
{
"env": [
{
"name": "JWS_ADMIN_USERNAME",
"value": "${JWS_ADMIN_USERNAME}"
},
{
"name": "JWS_ADMIN_PASSWORD",
"value": "${JWS_ADMIN_PASSWORD}"
},
{
"name": "HAWKULAR_APM_URI",
"value": "${HAWKULAR_APM_URI}"
},
{
"name": "HAWKULAR_APM_USERNAME",
"value": "${HAWKULAR_APM_USERNAME}"
},
{
"name": "HAWKULAR_APM_PASSWORD",
"value": "${HAWKULAR_APM_PASSWORD}"
},
{
"name": "JAVA_OPTS",
"value": "${JAVA_OPTS}"
},
{
"name": "MAVEN_MIRROR_URL",
"value": "${MAVEN_MIRROR_URL}"
}
],
"image": "${APPLICATION_NAME}",
"imagePullPolicy": "Always",
"name": "${APPLICATION_NAME}",
"ports": [
{
"containerPort": 8778,
"name": "jolokia",
"protocol": "TCP"
},
{
"containerPort": 8080,
"name": "http",
"protocol": "TCP"
}
],
"readinessProbe": {
"exec": {
"command": [
"/bin/bash",
"-c",
"curl -s -u ${JWS_ADMIN_USERNAME}:${JWS_ADMIN_PASSWORD} 'http://localhost:8080/manager/jmxproxy/?get=Catalina%3Atype%3DServer\u0026att=stateName' |grep -iq 'stateName *= *STARTED'"
]
}
}
}
],
"terminationGracePeriodSeconds": 60
}
},
"triggers": [
{
"imageChangeParams": {
"automatic": true,
"containerNames": [
"${APPLICATION_NAME}"
],
"from": {
"kind": "ImageStreamTag",
"name": "${APPLICATION_NAME}:latest"
}
},
"type": "ImageChange"
},
{
"type": "ConfigChange"
}
]
}
}
],
"parameters": [
{
"name": "APPLICATION_NAME",
"description": "The name for the application.",
"value": "mybank",
"required": true
},
{
"name": "HOSTNAME_HTTP",
"description": "Custom hostname for http service route. Leave blank for default hostname, e.g.: \u003capplication-name\u003e-\u003cproject\u003e.\u003cdefault-domain-suffix\u003e"
},
{
"name": "SOURCE_REPOSITORY_URL",
"description": "Git source URI for application",
"value": "http://git.example.com/git/mybank.git",
"required": true
},
{
"name": "SOURCE_REPOSITORY_REF",
"description": "Git branch/tag reference",
"value": "master"
},
{
"name": "CONTEXT_DIR",
"description": "Path within Git project to build; empty for root project directory.",
"value": "/"
},
{
"name": "JWS_ADMIN_USERNAME",
"description": "JWS Admin User",
"generate": "expression",
"from": "[a-zA-Z0-9]{8}",
"required": true
},
{
"name": "JWS_ADMIN_PASSWORD",
"description": "JWS Admin Password",
"generate": "expression",
"from": "[a-zA-Z0-9]{8}",
"required": true
},
{
"name": "GITHUB_WEBHOOK_SECRET",
"description": "GitHub trigger secret",
"generate": "expression",
"from": "[a-zA-Z0-9]{8}",
"required": true
},
{
"name": "GENERIC_WEBHOOK_SECRET",
"description": "Generic build trigger secret",
"generate": "expression",
"from": "[a-zA-Z0-9]{8}",
"required": true
},
{
"name": "IMAGE_STREAM_NAMESPACE",
"description": "Namespace in which the ImageStreams for Red Hat Middleware images are installed. These ImageStreams are normally installed in the openshift namespace. You should only need to modify this if you've installed the ImageStreams in a different namespace/project.",
"value": "openshift",
"required": true
},
{
"name": "HAWKULAR_APM_URI",
"description": "hawkular apm uri",
"value": "http://hawkular-apm-hawkular.apps.example.com",
"required": true
},
{
"name": "HAWKULAR_APM_USERNAME",
"description": "hawkular apm username",
"value": "admin",
"required": true
},
{
"name": "HAWKULAR_APM_PASSWORD",
"description": "hawkular apm password",
"value": "password",
"required": true
},
{
"name": "JAVA_OPTS",
"description": "java options",
"value": "-javaagent:/home/jboss/hawkular-apm-agent-opentracing.jar=boot:/home/jboss/hawkular-apm-agent-opentracing.jar -Djboss.modules.system.pkgs=org.jboss.byteman,org.hawkular.apm.agent.opentracing,io.opentracing,org.hawkular.apm.client.opentracing",
"required": true
},
{
"name": "MAVEN_MIRROR_URL",
"description": "maven mirror url",
"value": "http://192.168.56.1:8081/nexus/content/groups/public/",
"required": true
}
],
"labels": {
"template": "tomcat8-hawkular-apm-s2i"
}
}
5. 选择 tomcat8-hawkluar-apm-s2i 模板,发布应用
经过前面的“艰苦努力”,现在发布应用变得超级简单!
并且发布的应用,可以使用 Hawkular APM 监控,真是太棒了!
6. 清理并重做
如果有错,执行以下命令清理,然后重新执行上述步骤
oc delete bc/mybank is/mybank dc/mybank routes/mybank svc/mybank
oc delete is tomcat8-hawkular-apm -n openshift
oc delete template tomcat8-hawkluar-apm-s2i -n openshift
docker rmi registry.example.com:5000/maping930883/tomcat8-hawkular-apm:latest
参考文献:
1. https://blog.openshift.com/performance-metrics-apm-spring-boot-microservices-openshift/
2. https://github.com/lbroudoux/spring-boot-hello
使用 Dockerfile 方式部署 Java Web 应用太麻烦,而且不通用。
本文使用 Template 方式部署。
1. 创建 Builder Image
mkdir tomcat8-hawkular-apm
cd tomcat8-hawkular-apm
vim Dockerfile
内容如下:
FROM registry.example.com:5000/jboss-webserver-3/webserver30-tomcat8-openshift:latest
COPY hawkular-apm-agent-opentracing.jar $HOME
USER root
RUN chmod 777 $HOME/hawkular-apm-agent-opentracing.jar
RUN chmod -R 777 $HOME
USER 1001
说明:这里以 jboss-webserver-3/webserver30-tomcat8-openshift:latest 作为 Base Image。
docker build -t="maping930883/tomcat8-hawkular-apm" .
2. 修改 Tag,并 Push 到本地镜像仓库
docker tag maping930883/tomcat8-hawkular-apm:latest registry.example.com:5000/maping930883/tomcat8-hawkular-apm:latest
docker push registry.example.com:5000/maping930883/tomcat8-hawkular-apm:latest
3. 创建 Image Stream
参考 jboss-webserver30-tomcat8-openshift Image Stream
oc export is jboss-webserver30-tomcat8-openshift -n openshift -o json
修改完后,创建自己的 Image Stream
oc create -f tomcat8-hawkular-apm-is.json -n openshift
其中 tomcat8-hawkular-apm-is.json 内容如下:
{
"kind": "ImageStream",
"apiVersion": "v1",
"metadata": {
"name": "tomcat8-hawkular-apm",
"creationTimestamp": null
},
"spec": {
"dockerImageRepository": "registry.example.com:5000/maping930883/tomcat8-hawkular-apm",
"tags": [
{
"name": "latest",
"annotations": null,
"from": {
"kind": "DockerImage",
"name": "registry.example.com:5000/maping930883/tomcat8-hawkular-apm"
},
"generation": 1,
"importPolicy": {
"insecure": true
}
}
]
}
}
确认 TAGS 已经打上,执行 oc get is tomcat8-hawkular-apm -n openshift
输出如下:
NAME DOCKER REPO TAGS UPDATED
tomcat8-hawkular-apm registry.example.com:5000/maping930883/tomcat8-hawkular-apm latest 3 hours ago
如果 TAGS 没打上,执行 oc import-image tomcat8-hawkular-apm --insecure -n openshift
4. 创建 Template
参考 jws30-tomcat8-basic-s2i 模板
oc export template jws30-tomcat8-basic-s2i -n openshift -o json
修改 jws30-tomcat8-basic-s2i 模板
oc edit template jws30-tomcat8-basic-s2i -n openshift
把 name: jboss-webserver30-tomcat8-openshift:1.2
改为 name: jboss-webserver30-tomcat8-openshift:latest
修改完后,创建自己的模板
oc create -f tomcat8-hawkular-apm-s2i-template.json -n openshift
其中 tomcat8-hawkular-apm-s2i-template.json 内容如下:
{
"kind": "Template",
"apiVersion": "v1",
"metadata": {
"name": "tomcat8-hawkluar-apm-s2i",
"creationTimestamp": null,
"annotations": {
"iconClass": "icon-java",
"description": "Application template for Java Web applications built using S2I and supporting Hawkular APM.",
"tags": "java,tomcat8,hawkular,apm",
"version": "1.0"
}
},
"objects": [
{
"apiVersion": "v1",
"kind": "Service",
"metadata": {
"annotations": {
"description": "The web server's http port."
},
"labels": {
"application": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
},
"spec": {
"ports": [
{
"port": 8080,
"targetPort": 8080
}
],
"selector": {
"deploymentConfig": "${APPLICATION_NAME}"
}
}
},
{
"apiVersion": "v1",
"id": "${APPLICATION_NAME}-http",
"kind": "Route",
"metadata": {
"annotations": {
"description": "Route for application's http service."
},
"labels": {
"application": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
},
"spec": {
"host": "${HOSTNAME_HTTP}",
"to": {
"name": "${APPLICATION_NAME}"
}
}
},
{
"apiVersion": "v1",
"kind": "ImageStream",
"metadata": {
"labels": {
"application": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
}
},
{
"apiVersion": "v1",
"kind": "BuildConfig",
"metadata": {
"labels": {
"application": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
},
"spec": {
"output": {
"to": {
"kind": "ImageStreamTag",
"name": "${APPLICATION_NAME}:latest"
}
},
"source": {
"contextDir": "${CONTEXT_DIR}",
"git": {
"ref": "${SOURCE_REPOSITORY_REF}",
"uri": "${SOURCE_REPOSITORY_URL}"
},
"type": "Git"
},
"strategy": {
"sourceStrategy": {
"forcePull": true,
"from": {
"kind": "ImageStreamTag",
"name": "tomcat8-hawkular-apm:latest",
"namespace": "${IMAGE_STREAM_NAMESPACE}"
},
"env": [
{
"name": "MAVEN_MIRROR_URL",
"value": "${MAVEN_MIRROR_URL}"
}
]
},
"type": "Source"
},
"triggers": [
{
"github": {
"secret": "${GITHUB_WEBHOOK_SECRET}"
},
"type": "GitHub"
},
{
"generic": {
"secret": "${GENERIC_WEBHOOK_SECRET}"
},
"type": "Generic"
},
{
"imageChange": {},
"type": "ImageChange"
},
{
"type": "ConfigChange"
}
]
}
},
{
"apiVersion": "v1",
"kind": "DeploymentConfig",
"metadata": {
"labels": {
"application": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
},
"spec": {
"replicas": 1,
"selector": {
"deploymentConfig": "${APPLICATION_NAME}"
},
"strategy": {
"type": "Recreate"
},
"template": {
"metadata": {
"labels": {
"application": "${APPLICATION_NAME}",
"deploymentConfig": "${APPLICATION_NAME}"
},
"name": "${APPLICATION_NAME}"
},
"spec": {
"containers": [
{
"env": [
{
"name": "JWS_ADMIN_USERNAME",
"value": "${JWS_ADMIN_USERNAME}"
},
{
"name": "JWS_ADMIN_PASSWORD",
"value": "${JWS_ADMIN_PASSWORD}"
},
{
"name": "HAWKULAR_APM_URI",
"value": "${HAWKULAR_APM_URI}"
},
{
"name": "HAWKULAR_APM_USERNAME",
"value": "${HAWKULAR_APM_USERNAME}"
},
{
"name": "HAWKULAR_APM_PASSWORD",
"value": "${HAWKULAR_APM_PASSWORD}"
},
{
"name": "JAVA_OPTS",
"value": "${JAVA_OPTS}"
},
{
"name": "MAVEN_MIRROR_URL",
"value": "${MAVEN_MIRROR_URL}"
}
],
"image": "${APPLICATION_NAME}",
"imagePullPolicy": "Always",
"name": "${APPLICATION_NAME}",
"ports": [
{
"containerPort": 8778,
"name": "jolokia",
"protocol": "TCP"
},
{
"containerPort": 8080,
"name": "http",
"protocol": "TCP"
}
],
"readinessProbe": {
"exec": {
"command": [
"/bin/bash",
"-c",
"curl -s -u ${JWS_ADMIN_USERNAME}:${JWS_ADMIN_PASSWORD} 'http://localhost:8080/manager/jmxproxy/?get=Catalina%3Atype%3DServer\u0026att=stateName' |grep -iq 'stateName *= *STARTED'"
]
}
}
}
],
"terminationGracePeriodSeconds": 60
}
},
"triggers": [
{
"imageChangeParams": {
"automatic": true,
"containerNames": [
"${APPLICATION_NAME}"
],
"from": {
"kind": "ImageStreamTag",
"name": "${APPLICATION_NAME}:latest"
}
},
"type": "ImageChange"
},
{
"type": "ConfigChange"
}
]
}
}
],
"parameters": [
{
"name": "APPLICATION_NAME",
"description": "The name for the application.",
"value": "mybank",
"required": true
},
{
"name": "HOSTNAME_HTTP",
"description": "Custom hostname for http service route. Leave blank for default hostname, e.g.: \u003capplication-name\u003e-\u003cproject\u003e.\u003cdefault-domain-suffix\u003e"
},
{
"name": "SOURCE_REPOSITORY_URL",
"description": "Git source URI for application",
"value": "http://git.example.com/git/mybank.git",
"required": true
},
{
"name": "SOURCE_REPOSITORY_REF",
"description": "Git branch/tag reference",
"value": "master"
},
{
"name": "CONTEXT_DIR",
"description": "Path within Git project to build; empty for root project directory.",
"value": "/"
},
{
"name": "JWS_ADMIN_USERNAME",
"description": "JWS Admin User",
"generate": "expression",
"from": "[a-zA-Z0-9]{8}",
"required": true
},
{
"name": "JWS_ADMIN_PASSWORD",
"description": "JWS Admin Password",
"generate": "expression",
"from": "[a-zA-Z0-9]{8}",
"required": true
},
{
"name": "GITHUB_WEBHOOK_SECRET",
"description": "GitHub trigger secret",
"generate": "expression",
"from": "[a-zA-Z0-9]{8}",
"required": true
},
{
"name": "GENERIC_WEBHOOK_SECRET",
"description": "Generic build trigger secret",
"generate": "expression",
"from": "[a-zA-Z0-9]{8}",
"required": true
},
{
"name": "IMAGE_STREAM_NAMESPACE",
"description": "Namespace in which the ImageStreams for Red Hat Middleware images are installed. These ImageStreams are normally installed in the openshift namespace. You should only need to modify this if you've installed the ImageStreams in a different namespace/project.",
"value": "openshift",
"required": true
},
{
"name": "HAWKULAR_APM_URI",
"description": "hawkular apm uri",
"value": "http://hawkular-apm-hawkular.apps.example.com",
"required": true
},
{
"name": "HAWKULAR_APM_USERNAME",
"description": "hawkular apm username",
"value": "admin",
"required": true
},
{
"name": "HAWKULAR_APM_PASSWORD",
"description": "hawkular apm password",
"value": "password",
"required": true
},
{
"name": "JAVA_OPTS",
"description": "java options",
"value": "-javaagent:/home/jboss/hawkular-apm-agent-opentracing.jar=boot:/home/jboss/hawkular-apm-agent-opentracing.jar -Djboss.modules.system.pkgs=org.jboss.byteman,org.hawkular.apm.agent.opentracing,io.opentracing,org.hawkular.apm.client.opentracing",
"required": true
},
{
"name": "MAVEN_MIRROR_URL",
"description": "maven mirror url",
"value": "http://192.168.56.1:8081/nexus/content/groups/public/",
"required": true
}
],
"labels": {
"template": "tomcat8-hawkular-apm-s2i"
}
}
5. 选择 tomcat8-hawkluar-apm-s2i 模板,发布应用
经过前面的“艰苦努力”,现在发布应用变得超级简单!
并且发布的应用,可以使用 Hawkular APM 监控,真是太棒了!
6. 清理并重做
如果有错,执行以下命令清理,然后重新执行上述步骤
oc delete bc/mybank is/mybank dc/mybank routes/mybank svc/mybank
oc delete is tomcat8-hawkular-apm -n openshift
oc delete template tomcat8-hawkluar-apm-s2i -n openshift
docker rmi registry.example.com:5000/maping930883/tomcat8-hawkular-apm:latest
参考文献:
1. https://blog.openshift.com/performance-metrics-apm-spring-boot-microservices-openshift/
2. https://github.com/lbroudoux/spring-boot-hello
2017年3月16日星期四
OpenShift_066:使用 Hawkular APM 监控容器中的 Java Web 应用(Dockerfile 方式)
环境:OCP 3.4
1. 拷贝 .war 和 hawkluar apm jar 文件到 Master 机器上 (在 MAC 机器上操作)
scp example.war root@master.example.com:/opt/
scp hawkular-apm-agent-opentracing.jar hawkular-apm-agent.jar root@master.example.com:/opt/
2. 编写 Dockerfile(在 Master 机器上操作)
cd /opt
mkdir example
cd example
mv /opt/example.war .
mv /opt/hawkular-apm-agent-opentracing.jar .
mv /opt/hawkular-apm-agent.jar .
vim Dockerfile
内容如下:
FROM registry.example.com:5000/jboss-webserver-3/webserver30-tomcat8-openshift:latest
USER root
COPY example.war $JWS_HOME/webapps/ROOT.war
COPY hawkular-apm-agent.jar $HOME
COPY hawkular-apm-agent-opentracing.jar $HOME
#ENV JAVA_OPTS -javaagent:$HOME/hawkular-apm-agent.jar=boot:$HOME/hawkular-apm-agent.jar -Djboss.modules.system.pkgs=org.jboss.byteman,org.hawkular.apm.instrumenter,org.hawkular.apm.client.collector
ENV JAVA_OPTS -javaagent:$HOME/hawkular-apm-agent-opentracing.jar=boot:$HOME/hawkular-apm-agent-opentracing.jar -Djboss.modules.system.pkgs=org.jboss.byteman,org.hawkular.apm.agent.opentracing,io.opentracing,org.hawkular.apm.client.opentracing
ENV HAWKULAR_APM_URI=http://hawkular-apm-hawkular.apps.example.com:80
ENV HAWKULAR_APM_USERNAME=admin
ENV HAWKULAR_APM_PASSWORD=password
注意,这里使用 jboss-webserver-3/webserver30-tomcat8-openshift 作为 Base Image,因此请先确认该基础镜像部署成功。
如需帮助,请参考《使用 binary 方式部署 .war 到 Tomcat 8 》 。
3. 部署 example 应用
cd .. 退到 example 上一级目录
oc login -u admin -p admin
创建应用
oc new-app example --name=example --insecure-registry=true
输出略。
开始 build
oc start-build example --from-dir=example
输出略。
查看日志,确认 build 成功。
oc logs example-1-build
输出略。
5. 创建 route
oc expose svc example
如果有错,执行以下命令清理:
oc delete bc/example is/example dc/example svc/example routes/example is/webserver30-tomcat8-openshift
6. 访问 http://example.apps.example.com/index.jsp
7. 查看 https://hawkular-apm-hawkular.apps.example.com
参考文献:
1. https://hawkular.gitbooks.io/hawkular-apm-user-guide/content/instrumentation/jvmagent.html
1. 拷贝 .war 和 hawkluar apm jar 文件到 Master 机器上 (在 MAC 机器上操作)
scp example.war root@master.example.com:/opt/
scp hawkular-apm-agent-opentracing.jar hawkular-apm-agent.jar root@master.example.com:/opt/
2. 编写 Dockerfile(在 Master 机器上操作)
cd /opt
mkdir example
cd example
mv /opt/example.war .
mv /opt/hawkular-apm-agent-opentracing.jar .
mv /opt/hawkular-apm-agent.jar .
vim Dockerfile
内容如下:
FROM registry.example.com:5000/jboss-webserver-3/webserver30-tomcat8-openshift:latest
USER root
COPY example.war $JWS_HOME/webapps/ROOT.war
COPY hawkular-apm-agent.jar $HOME
COPY hawkular-apm-agent-opentracing.jar $HOME
#ENV JAVA_OPTS -javaagent:$HOME/hawkular-apm-agent.jar=boot:$HOME/hawkular-apm-agent.jar -Djboss.modules.system.pkgs=org.jboss.byteman,org.hawkular.apm.instrumenter,org.hawkular.apm.client.collector
ENV JAVA_OPTS -javaagent:$HOME/hawkular-apm-agent-opentracing.jar=boot:$HOME/hawkular-apm-agent-opentracing.jar -Djboss.modules.system.pkgs=org.jboss.byteman,org.hawkular.apm.agent.opentracing,io.opentracing,org.hawkular.apm.client.opentracing
ENV HAWKULAR_APM_URI=http://hawkular-apm-hawkular.apps.example.com:80
ENV HAWKULAR_APM_USERNAME=admin
ENV HAWKULAR_APM_PASSWORD=password
注意,这里使用 jboss-webserver-3/webserver30-tomcat8-openshift 作为 Base Image,因此请先确认该基础镜像部署成功。
如需帮助,请参考《使用 binary 方式部署 .war 到 Tomcat 8 》 。
3. 部署 example 应用
cd .. 退到 example 上一级目录
oc login -u admin -p admin
创建应用
oc new-app example --name=example --insecure-registry=true
输出略。
开始 build
oc start-build example --from-dir=example
输出略。
查看日志,确认 build 成功。
oc logs example-1-build
输出略。
5. 创建 route
oc expose svc example
如果有错,执行以下命令清理:
oc delete bc/example is/example dc/example svc/example routes/example is/webserver30-tomcat8-openshift
6. 访问 http://example.apps.example.com/index.jsp
7. 查看 https://hawkular-apm-hawkular.apps.example.com
参考文献:
1. https://hawkular.gitbooks.io/hawkular-apm-user-guide/content/instrumentation/jvmagent.html
OpenShift_065:离线部署 Hawkular APM(Template 方式)
环境:OCP 3.4
之前按照《离线部署 Hawkular APM(Dockerfile 方式)》部署 Hawkular APM 比较麻烦,而且管理员账户/口令,在 pod 重启以后,每次都变,很不方便。
部署 Hawkular APM 更好的方式是使用 Template 方式。
需要特别说明的是,运行 Hawkular APM 的 node 节点最小配置为 2c 4G,否则运行不起来。
1. 下载基础镜像 (在 MAC 机器上操作)
docker pull jpkroehling/elasticsearch
docker pull jboss/hawkular-apm-server
docker save -o hawkular.tar.gz jpkroehling/elasticsearch jboss/hawkular-apm-server
scp hawkular.tar.gz root@192.168.56.112:/opt/ose/images/
2. 加载基础镜像(在 Registry 机器上操作)
docker load -i hawkular.tar.gz
docker tag jpkroehling/elasticsearch registry.example.com:5000/jpkroehling/elasticsearch
docker push registry.example.com:5000/jpkroehling/elasticsearch
docker tag jboss/hawkular-apm-server registry.example.com:5000/jboss/hawkular-apm-server
docker push registry.example.com:5000/jboss/hawkular-apm-server
3. 克隆 hawkular-apm 项目(之前已经把 hawkular-apm 项目放到 git.example.com 上)
cd /tmp
git clone http://git.example.com/git/hawkular-apm.git/;
cd hawkular-apm/openshift-templates
4. 修改 hawkular-apm-server-deployment.yml 和 hawkular-apm-server.yml 文件内容
把 image 的路径前面都增加 registry.example.com:5000/ 前缀
5. 创建 hawkular-apm-server
oc create -f hawkular-apm-server-deployment.yml
注意:此种方式默认的管理员账户/口令是 admin/password,是不能修改的,如果想要修改请按照步骤 6 操作。
如果有错,执行如下命令清除:
oc delete secrets hawkular-apm-admin-account
oc delete route hawkular-apm
oc delete dc hawkular-apm hawkular-apm-es
oc delete sa hawkular-apm hawkular-apm-es
oc delete svc hawkular-apm hawkular-apm-es
6. 创建 hawkular-apm-server template
oc login -u system:admin
oc create -n openshift -f hawkular-apm-server.yml
7. 根据 template 在控制台创建 hawkular-apm-server
oc new-project hawkular
管理员账户和口令可以由你指定。
参考文献:
1. http://www.hawkular.org/blog/2016/07/14/hawkular-apm-openshift.html
之前按照《离线部署 Hawkular APM(Dockerfile 方式)》部署 Hawkular APM 比较麻烦,而且管理员账户/口令,在 pod 重启以后,每次都变,很不方便。
部署 Hawkular APM 更好的方式是使用 Template 方式。
需要特别说明的是,运行 Hawkular APM 的 node 节点最小配置为 2c 4G,否则运行不起来。
1. 下载基础镜像 (在 MAC 机器上操作)
docker pull jpkroehling/elasticsearch
docker pull jboss/hawkular-apm-server
docker save -o hawkular.tar.gz jpkroehling/elasticsearch jboss/hawkular-apm-server
scp hawkular.tar.gz root@192.168.56.112:/opt/ose/images/
2. 加载基础镜像(在 Registry 机器上操作)
docker load -i hawkular.tar.gz
docker tag jpkroehling/elasticsearch registry.example.com:5000/jpkroehling/elasticsearch
docker push registry.example.com:5000/jpkroehling/elasticsearch
docker tag jboss/hawkular-apm-server registry.example.com:5000/jboss/hawkular-apm-server
docker push registry.example.com:5000/jboss/hawkular-apm-server
3. 克隆 hawkular-apm 项目(之前已经把 hawkular-apm 项目放到 git.example.com 上)
cd /tmp
git clone http://git.example.com/git/hawkular-apm.git/;
cd hawkular-apm/openshift-templates
4. 修改 hawkular-apm-server-deployment.yml 和 hawkular-apm-server.yml 文件内容
把 image 的路径前面都增加 registry.example.com:5000/ 前缀
5. 创建 hawkular-apm-server
oc create -f hawkular-apm-server-deployment.yml
注意:此种方式默认的管理员账户/口令是 admin/password,是不能修改的,如果想要修改请按照步骤 6 操作。
如果有错,执行如下命令清除:
oc delete secrets hawkular-apm-admin-account
oc delete route hawkular-apm
oc delete dc hawkular-apm hawkular-apm-es
oc delete sa hawkular-apm hawkular-apm-es
oc delete svc hawkular-apm hawkular-apm-es
6. 创建 hawkular-apm-server template
oc login -u system:admin
oc create -n openshift -f hawkular-apm-server.yml
7. 根据 template 在控制台创建 hawkular-apm-server
oc new-project hawkular
管理员账户和口令可以由你指定。
参考文献:
1. http://www.hawkular.org/blog/2016/07/14/hawkular-apm-openshift.html
2017年3月15日星期三
OpenShift_064:如何访问私有 git 仓库?
环境:OCP 3.4
注意,本文步骤尚未实验证实,因为没有私有 git 仓库,等我用 Gogs 搭建一个私有 git 仓库后,再进行细节验证。
大多数 git 仓库都允许免认证 clone,但私有 git 仓库需要认证通过才可以 clone。
1. 创建应用
oc new-app openshift/php~git@github.com:christianh814/php-example-ose3.git
输出如下:
查看 build 日志,发现有错,原因是没有权限 clone 代码。
oc build-logs php-example-ose3-1
输出如下:
2. 生成一个 rsa 公钥/私钥对
ssh-keygen -t rsa -C “maping930883@hotmail.com"
注意不要覆盖 ~/.ssh/ 目录下已有的 id_rsa 和 id_rsa.pub 文件。
3. 把公钥 id_rsa.pub 文件内容复制粘贴到你的 git 仓库账号设置中
4. 根据私钥 id_rsa 文件创建 secret:scmsecret
oc secrets new scmsecret ssh-privatekey=$HOME/.ssh/id_rsa
输出如下:
secret/scmsecret
5. 把 secret 增加到 builder sa 中,这样 builder sa 可以克隆源代码
对于 OpenShift 3.2,使用
oc secrets add serviceaccount/builder secrets/scmsecret
对于 OpenShift 3.3,使用
oc secrets link builder scmsecret
6. 把 secret 添加到 buildConfig 中
oc patch buildConfig php-example-ose3 -p '{"spec":{"source":{"sourceSecret":{"name":"scmsecret"}}}}'
输出如下:
确认 bc 确实添加了 secret
oc get bc/php-example-ose3 -o json
输出如下:
7. 再次 build 应用,这次成功了
oc start-build php-example-ose3
8. 创建 route
oc expose svc/php-example-ose3
参考文献:
1. https://blog.openshift.com/deploying-from-private-git-repositories/
2. https://blog.openshift.com/using-ssh-key-for-s2i-builds/
3. https://docs.openshift.com/online/dev_guide/builds/index.html#ssh-key-authentication
注意,本文步骤尚未实验证实,因为没有私有 git 仓库,等我用 Gogs 搭建一个私有 git 仓库后,再进行细节验证。
大多数 git 仓库都允许免认证 clone,但私有 git 仓库需要认证通过才可以 clone。
1. 创建应用
oc new-app openshift/php~git@github.com:christianh814/php-example-ose3.git
输出如下:
查看 build 日志,发现有错,原因是没有权限 clone 代码。
oc build-logs php-example-ose3-1
输出如下:
2. 生成一个 rsa 公钥/私钥对
ssh-keygen -t rsa -C “maping930883@hotmail.com"
注意不要覆盖 ~/.ssh/ 目录下已有的 id_rsa 和 id_rsa.pub 文件。
3. 把公钥 id_rsa.pub 文件内容复制粘贴到你的 git 仓库账号设置中
4. 根据私钥 id_rsa 文件创建 secret:scmsecret
oc secrets new scmsecret ssh-privatekey=$HOME/.ssh/id_rsa
输出如下:
secret/scmsecret
5. 把 secret 增加到 builder sa 中,这样 builder sa 可以克隆源代码
对于 OpenShift 3.2,使用
oc secrets add serviceaccount/builder secrets/scmsecret
对于 OpenShift 3.3,使用
oc secrets link builder scmsecret
6. 把 secret 添加到 buildConfig 中
oc patch buildConfig php-example-ose3 -p '{"spec":{"source":{"sourceSecret":{"name":"scmsecret"}}}}'
输出如下:
确认 bc 确实添加了 secret
oc get bc/php-example-ose3 -o json
输出如下:
7. 再次 build 应用,这次成功了
oc start-build php-example-ose3
8. 创建 route
oc expose svc/php-example-ose3
参考文献:
1. https://blog.openshift.com/deploying-from-private-git-repositories/
2. https://blog.openshift.com/using-ssh-key-for-s2i-builds/
3. https://docs.openshift.com/online/dev_guide/builds/index.html#ssh-key-authentication
OpenShift_063:远程调试容器中的 Java Web 应用
环境:OCP 3.4 + Eclipse Neon.2 Release (4.6.2) + JBoss Tools 4.4.3
本文以 mybank 应用为例,说明如何远程调试容器中的 Java Web 应用,因此请先部署好 mybank 应用。
关于部署 mybank 应用,请参考《OpenShift_031:部署 MyBank 到 JBoss EAP 7》。
1. 下载并安装 Eclipse
下载地址:https://www.eclipse.org/downloads/eclipse-packages/
介质:eclipse-jee-neon-2-macosx-cocoa-x86_64.tar.gz
2. 下载 JBoss Tools Plugin
下载地址:http://tools.jboss.org/downloads/jbosstools/
介质:jbosstools-4.4.3.Final-updatesite-core.zip
3. 离线安装 JBoss Tools Plugin
(1)打开 Eclipse
(2)点击 Help -> Install New Software
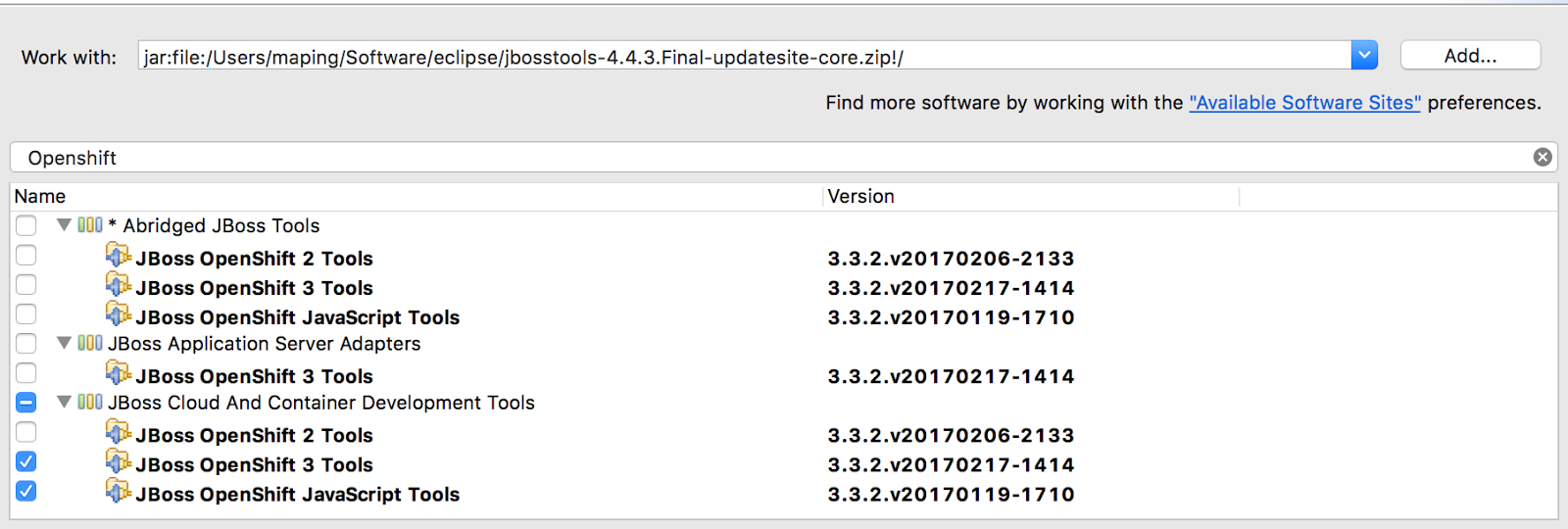
(3)点击 Work with 旁边的 Add,点击 Archive,选择 jbosstools-4.4.3.Final-updatesite-core.zip
(4)输入 OpenShift,只勾选与 OpenShift 3 相关的 Tools
4. 如果觉得 Eclipse + JBoss Tools Plugin 安装比较麻烦,可以用 Redhat JBoss Developer Studio 10.3.0
好处是 JBoss Developer Studio 已经都给你配好了,装完无需配置即可使用。
下载地址:https://developers.redhat.com/products/devstudio/download/
安装介质:devstudio-10.3.0.GA-installer-standalone.jar
5. 配置 OpenShift Server
参考《Eclipse + JBoss Tools Plugin 配置 Openshift 集成开发环境配置》
6. 右键应用 mybank,生成 Server Adapter...
右键刚刚生成 mybank at OpenShift 3 ....,点击 Start,
修改页面代码,比如换个图片,直接刷新页面,发现代码已经同步到容器中了。
无需重新生成新的镜像并且发布,和在本地开发调试的感觉几乎一样,真是太方便了!
说明:修改代码或者手动 Restart/Publish 后,会自动重新部署 ROOT.war,不会重启 EAP,更不会重新创建 Pod。
也就是说,Server Adapter 是连接到了容器中的 EAP Server(即下图中的 mybank at OpenShift 3...),然后做重新部署。
经过进一步测试,修改前端页面和后端 Java 代码,都只要等待自动重新部署 ROOT.war 完成之后,刷新页面即可。
因此,也就不需要区分增量发布和全量发布了。
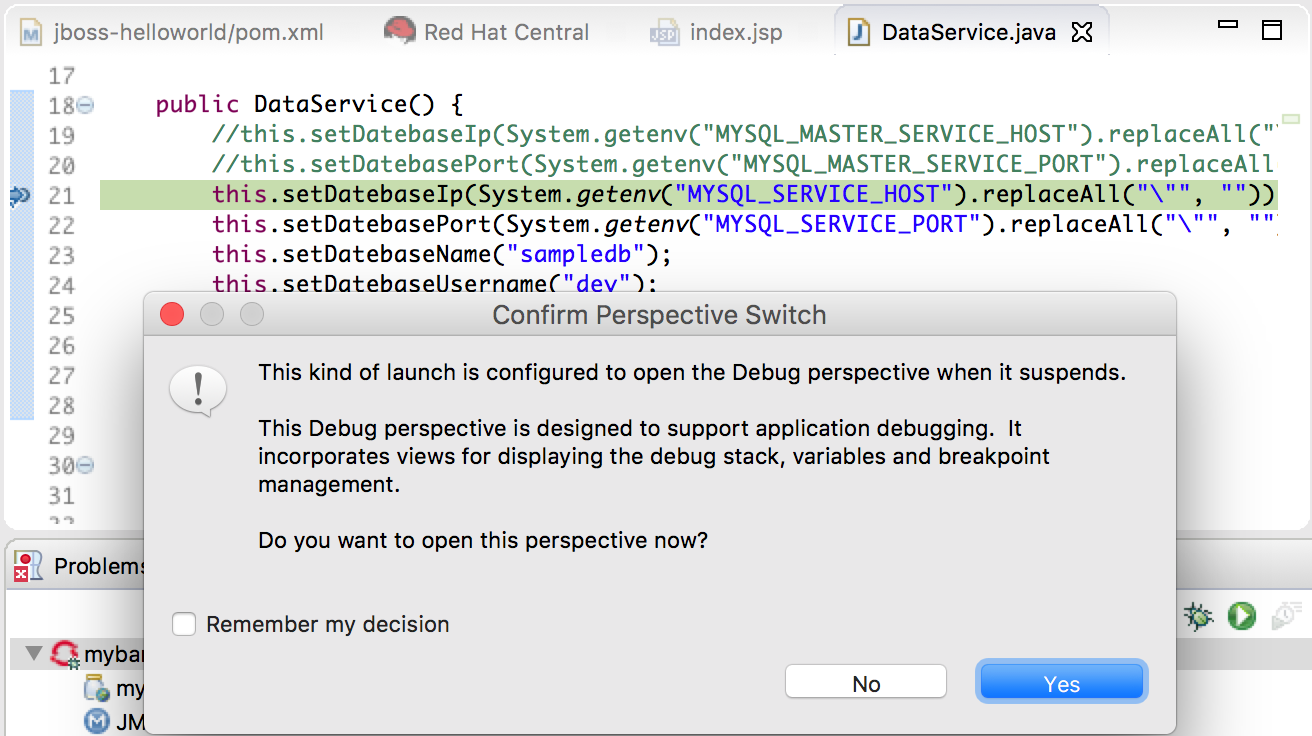
7. 右键刚刚生成 mybank at OpenShift 3 ....,点击 Restart in Debug
笔者发现,只要不切换启动模式重启,容器不会重新创建,这也大大提高了开发效率。
这里是因为从普通模式切换到了 Debug 模式,因此会销毁旧 pod,并重新创建一个新 pod。
8. 克隆 mybank 应用
参考《配置 Web Hook 自动开始新 Build》。
9. 在代码中设置断点,刷新页面,触发断点
参考文献:
1. https://developers.redhat.com/blog/2016/07/21/debugging-java-applications-using-the-red-hat-container-development-kit/
2. https://vimeo.com/44548968
本文以 mybank 应用为例,说明如何远程调试容器中的 Java Web 应用,因此请先部署好 mybank 应用。
关于部署 mybank 应用,请参考《OpenShift_031:部署 MyBank 到 JBoss EAP 7》。
1. 下载并安装 Eclipse
下载地址:https://www.eclipse.org/downloads/eclipse-packages/
介质:eclipse-jee-neon-2-macosx-cocoa-x86_64.tar.gz
2. 下载 JBoss Tools Plugin
下载地址:http://tools.jboss.org/downloads/jbosstools/
介质:jbosstools-4.4.3.Final-updatesite-core.zip
3. 离线安装 JBoss Tools Plugin
(1)打开 Eclipse
(2)点击 Help -> Install New Software
(3)点击 Work with 旁边的 Add,点击 Archive,选择 jbosstools-4.4.3.Final-updatesite-core.zip
(4)输入 OpenShift,只勾选与 OpenShift 3 相关的 Tools
4. 如果觉得 Eclipse + JBoss Tools Plugin 安装比较麻烦,可以用 Redhat JBoss Developer Studio 10.3.0
好处是 JBoss Developer Studio 已经都给你配好了,装完无需配置即可使用。
下载地址:https://developers.redhat.com/products/devstudio/download/
安装介质:devstudio-10.3.0.GA-installer-standalone.jar
5. 配置 OpenShift Server
参考《Eclipse + JBoss Tools Plugin 配置 Openshift 集成开发环境配置》
6. 右键应用 mybank,生成 Server Adapter...
右键刚刚生成 mybank at OpenShift 3 ....,点击 Start,
修改页面代码,比如换个图片,直接刷新页面,发现代码已经同步到容器中了。
无需重新生成新的镜像并且发布,和在本地开发调试的感觉几乎一样,真是太方便了!
说明:修改代码或者手动 Restart/Publish 后,会自动重新部署 ROOT.war,不会重启 EAP,更不会重新创建 Pod。
也就是说,Server Adapter 是连接到了容器中的 EAP Server(即下图中的 mybank at OpenShift 3...),然后做重新部署。
经过进一步测试,修改前端页面和后端 Java 代码,都只要等待自动重新部署 ROOT.war 完成之后,刷新页面即可。
因此,也就不需要区分增量发布和全量发布了。
7. 右键刚刚生成 mybank at OpenShift 3 ....,点击 Restart in Debug
笔者发现,只要不切换启动模式重启,容器不会重新创建,这也大大提高了开发效率。
这里是因为从普通模式切换到了 Debug 模式,因此会销毁旧 pod,并重新创建一个新 pod。
8. 克隆 mybank 应用
参考《配置 Web Hook 自动开始新 Build》。
9. 在代码中设置断点,刷新页面,触发断点
参考文献:
1. https://developers.redhat.com/blog/2016/07/21/debugging-java-applications-using-the-red-hat-container-development-kit/
2. https://vimeo.com/44548968
2017年3月14日星期二
OpenShift_062:离线部署 Hawkular APM(Dockerfile 方式)
环境:MAC OS X 10.12.3 + OpenShift 3.4 + Hawkular APM 0.14.0.Final
与《部署 Hawkular APM 到 OpenShift Origin》的区别是,本文是部署到 OpenShift 3.4 企业版上。
由于 OpenShift 是在内网,所以需要离线部署。
1. 下载基础镜像 (在 MAC 机器上操作)
docker pull jboss/base-jdk:8
docker save -o base-jdk.tar.gz jboss/base-jdk:8
scp base-jdk.tar.gz root@192.168.56.112:/opt/ose/images/
2. 加载基础镜像(在 Registry 机器上操作)
docker load -i base-jdk.tar.gz
docker tag jboss/base-jdk:8 registry.example.com:5000/jboss/base-jdk:8
docker push registry.example.com:5000/jboss/base-jdk:8
3. 克隆 hawkular-apm(在 MAC 机器上操作)
cd ~/mygit/redhat-helloworld-msa
git clone https://github.com/jboss-dockerfiles/hawkular-apm.git (已做)
cd hawkular-apm/hawkular-apm-server
修改 Dockerfile
把 ENV HAWKULAR_APM_VERSION 0.14.1.Final
改为 ENV HAWKULAR_APM_VERSION 0.14.0.Final
把从网上下载 hawkular-apm-dist-0.14.0.Final.zip 改为从本地拷贝
# Download Hawkular-APM from github
COPY hawkular-apm-dist-$HAWKULAR_APM_VERSION.zip $HOME
RUN cd $HOME \
# && curl -O -L https://github.com/hawkular/hawkular-apm/releases/download/$HAWKULAR_APM_VERSION/hawkular-apm-dist-$HAWKULAR_APM_VERSION.zip \
&& unzip -d $JBOSS_HOME hawkular-apm-dist-$HAWKULAR_APM_VERSION.zip \
&& rm hawkular-apm-dist-$HAWKULAR_APM_VERSION.zip
cp ~/Tools/hawkular/apm/hawkular-apm-dist-0.14.0.Final.zip .
4. 拷贝到 Registry 机器上(在 MAC 机器上操作)
cd ~/mygit/redhat-helloworld-msa
scp -r hawkular-apm/ root@registry.example.com:/opt/hawkular-apm-demo
5. 初始化 mybank git 仓库(在 Registry 机器上操作)mkdir -p /opt/git/repo/hawkular-apm.git;
cd /opt/git/repo/hawkular-apm.git;
git init --bare;
git update-server-info;
mv hooks/post-update.sample hooks/post-update;
6. 拷贝 hawkular-apm 代码,并提交(在 Registry 机器上操作)
cd /opt;
git clone file:///opt/git/repo/hawkular-apm.git/;
cp hawkular-apm-demo/* hawkular-apm -rf;
cp hawkular-apm-demo/.sti hawkular-apm -rf;
cp hawkular-apm-demo/.htaccess hawkular-apm -rf;
cp hawkular-apm-demo/.gitignore hawkular-apm -rf;
cd hawkular-apm;
git add .;
git commit -m 'initial upload';
git push origin master;
7. 验证 hawkular-apm git 仓库是否创建成功(在 Master 机器上操作)
cd /tmp;
git clone http://git.example.com/git/hawkular-apm.git/;
8. 部署 Hawkular APM (在 Master 机器上操作)
cd /tmp/hawkular-apm/hawkular-apm-server
oc new-build --binary --name=hawkular-apm-serveroc start-build hawkular-apm-server --from-dir=. --follow
oc new-app hawkular-apm-server
oc expose service hawkular-apm-server
9. 部署 Hawkular APM
oc get pod
输出如下:
NAME READY STATUS RESTARTS AGE
hawkular-apm-server-1-52jfr 1/1 Running 0 5m
hawkular-apm-server-1-build 0/1 Completed 0 9m
oc logs hawkular-apm-server-1-52jfr
查找到如下信息:
Username: adminCXhaeqO
Password: 6jRJI3zu8fF08Fc4X
oc get route
输出如下:
NAME HOST/PORT PATH SERVICES PORT TERMINATION
hawkular-apm-server hawkular-apm-server-applications.apps.example.com hawkular-apm-server 8080-tcp
10. 启动 JBoss EAP 7 (已经部署 jboss-helloworld 和 jboss-helloworld-mdb)
export HAWKULAR_APM_URI=hawkular-apm-server-applications.apps.example.com
export HAWKULAR_APM_USERNAME=adminCXhaeqO
export HAWKULAR_APM_PASSWORD=6jRJI3zu8fF08Fc4X
cd ~/Redhat/eap/demo/7.0/2017-02-04
. ~/setJdk8Env.sh
./jboss-eap-7.0/bin/standalone.sh -Djboss.server.base.dir=./myeap -c standalone-full.xml -Djboss.socket.binding.port-offset=10000
11. 访问 Hawkular APM
刷新 http://localhost:18080/jboss-helloworld/HelloWorld
刷新 http://localhost:18080/jboss-helloworld-mdb/HelloWorldMDBServletClient
刷新 http://hawkular-apm-server-applications.apps.example.com/
参考文献:
1. http://www.hawkular.org/blog/2016/11/25/hawkular-apm-on-openshift.html
2. http://www.hawkular.org/blog/2016/07/14/hawkular-apm-openshift.html
3. https://hawkular.gitbooks.io/hawkular-apm-user-guide/content/quickstart/
与《部署 Hawkular APM 到 OpenShift Origin》的区别是,本文是部署到 OpenShift 3.4 企业版上。
由于 OpenShift 是在内网,所以需要离线部署。
1. 下载基础镜像 (在 MAC 机器上操作)
docker pull jboss/base-jdk:8
docker save -o base-jdk.tar.gz jboss/base-jdk:8
scp base-jdk.tar.gz root@192.168.56.112:/opt/ose/images/
2. 加载基础镜像(在 Registry 机器上操作)
docker load -i base-jdk.tar.gz
docker tag jboss/base-jdk:8 registry.example.com:5000/jboss/base-jdk:8
docker push registry.example.com:5000/jboss/base-jdk:8
3. 克隆 hawkular-apm(在 MAC 机器上操作)
cd ~/mygit/redhat-helloworld-msa
git clone https://github.com/jboss-dockerfiles/hawkular-apm.git (已做)
cd hawkular-apm/hawkular-apm-server
修改 Dockerfile
把 ENV HAWKULAR_APM_VERSION 0.14.1.Final
改为 ENV HAWKULAR_APM_VERSION 0.14.0.Final
把从网上下载 hawkular-apm-dist-0.14.0.Final.zip 改为从本地拷贝
# Download Hawkular-APM from github
COPY hawkular-apm-dist-$HAWKULAR_APM_VERSION.zip $HOME
RUN cd $HOME \
# && curl -O -L https://github.com/hawkular/hawkular-apm/releases/download/$HAWKULAR_APM_VERSION/hawkular-apm-dist-$HAWKULAR_APM_VERSION.zip \
&& unzip -d $JBOSS_HOME hawkular-apm-dist-$HAWKULAR_APM_VERSION.zip \
&& rm hawkular-apm-dist-$HAWKULAR_APM_VERSION.zip
cp ~/Tools/hawkular/apm/hawkular-apm-dist-0.14.0.Final.zip .
4. 拷贝到 Registry 机器上(在 MAC 机器上操作)
cd ~/mygit/redhat-helloworld-msa
scp -r hawkular-apm/ root@registry.example.com:/opt/hawkular-apm-demo
5. 初始化 mybank git 仓库(在 Registry 机器上操作)mkdir -p /opt/git/repo/hawkular-apm.git;
cd /opt/git/repo/hawkular-apm.git;
git init --bare;
git update-server-info;
mv hooks/post-update.sample hooks/post-update;
6. 拷贝 hawkular-apm 代码,并提交(在 Registry 机器上操作)
cd /opt;
git clone file:///opt/git/repo/hawkular-apm.git/;
cp hawkular-apm-demo/* hawkular-apm -rf;
cp hawkular-apm-demo/.sti hawkular-apm -rf;
cp hawkular-apm-demo/.htaccess hawkular-apm -rf;
cp hawkular-apm-demo/.gitignore hawkular-apm -rf;
cd hawkular-apm;
git add .;
git commit -m 'initial upload';
git push origin master;
7. 验证 hawkular-apm git 仓库是否创建成功(在 Master 机器上操作)
cd /tmp;
git clone http://git.example.com/git/hawkular-apm.git/;
8. 部署 Hawkular APM (在 Master 机器上操作)
cd /tmp/hawkular-apm/hawkular-apm-server
oc new-build --binary --name=hawkular-apm-serveroc start-build hawkular-apm-server --from-dir=. --follow
oc new-app hawkular-apm-server
oc expose service hawkular-apm-server
9. 部署 Hawkular APM
oc get pod
输出如下:
NAME READY STATUS RESTARTS AGE
hawkular-apm-server-1-52jfr 1/1 Running 0 5m
hawkular-apm-server-1-build 0/1 Completed 0 9m
oc logs hawkular-apm-server-1-52jfr
查找到如下信息:
Username: adminCXhaeqO
Password: 6jRJI3zu8fF08Fc4X
oc get route
输出如下:
NAME HOST/PORT PATH SERVICES PORT TERMINATION
hawkular-apm-server hawkular-apm-server-applications.apps.example.com hawkular-apm-server 8080-tcp
10. 启动 JBoss EAP 7 (已经部署 jboss-helloworld 和 jboss-helloworld-mdb)
export HAWKULAR_APM_URI=hawkular-apm-server-applications.apps.example.com
export HAWKULAR_APM_USERNAME=adminCXhaeqO
export HAWKULAR_APM_PASSWORD=6jRJI3zu8fF08Fc4X
cd ~/Redhat/eap/demo/7.0/2017-02-04
. ~/setJdk8Env.sh
./jboss-eap-7.0/bin/standalone.sh -Djboss.server.base.dir=./myeap -c standalone-full.xml -Djboss.socket.binding.port-offset=10000
11. 访问 Hawkular APM
刷新 http://localhost:18080/jboss-helloworld/HelloWorld
刷新 http://localhost:18080/jboss-helloworld-mdb/HelloWorldMDBServletClient
刷新 http://hawkular-apm-server-applications.apps.example.com/
参考文献:
1. http://www.hawkular.org/blog/2016/11/25/hawkular-apm-on-openshift.html
2. http://www.hawkular.org/blog/2016/07/14/hawkular-apm-openshift.html
3. https://hawkular.gitbooks.io/hawkular-apm-user-guide/content/quickstart/
订阅:
博文 (Atom)